
We’re all familiar with passports, driver’s licenses, and, of course, our personal identity cards. Many of us keep these as physical documents and carry them with us wherever we go. But with verifiable credentials, you can take them to even more places, including the digital world.
Think of it as a decentralised way of managing your identity. When used with decentralised identifiers, which is a new type of globally unique identifier, these cryptographically secure verifiable credentials will free you up from centralised entities or databases. You can choose how and when to use them for authentication purposes, something that can be helpful in Know-Your-Customer processes, or KYC.
Similar to how cryptocurrencies are enabling us to separate financial activities from central banks, verifiable credentials will enable us to manage our data away from big data organisations. However, for verifiable credentials to work, we still need an ecosystem in place. Some may call this the trust triangle, with the issuer, holder, and verifier as the main pillars of this ecosystem.
Read: How self-sovereign identity can change our digital lives
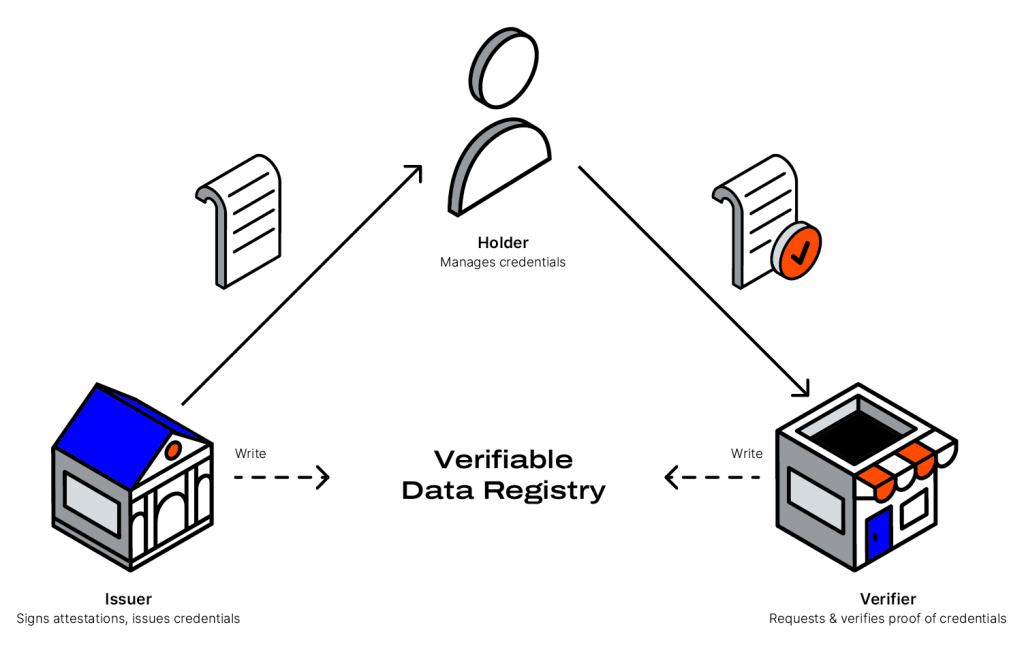
As shown in the above diagram, the issuer represents the entity asserting claims about you. This could be information about your birth, which would be presented in a birth certificate, or your level of education, which would be presented in, for example, your bachelor’s degree. Educational institutions and government bodies are just some examples of entities that can play the role of the issuer.
The holder is the one who manages the credentials. This could be you, the subject of those credentials. But not all subjects are holders. For instance, you could be the holder of health records regarding your pet, which in this case would be the subject of those credentials.
Finally, the verifier is usually the entity that wants to process your credentials. Credentials may be checked based on three aspects: competent authority, validity, and tamper-proof traits. Through the trust triangle, the verifier only needs to check your credentials against a verifiable data registry.
A verifiable data registry can facilitate the creation and mediation of decentralised identifiers, public keys, or other relevant data. It can exist in the form of a database, government ID databases, or a distributed ledger like blockchain.
Let’s take the example of the vaccination certificate. The hospital or government will issue the certificate to a person once they have gotten vaccinated. Here, the hospital or government authority is the issuer while the vaccinated person is the holder. Once the holder gets these credentials, they are converted into a verifiable presentation that is machine-readable, allowing details to be easily verified digitally.
UKISS Technology is developing a self-sovereign identity framework to support verifiable credentials and decentralised identifiers. It could just be the first identity framework supported by blockchain that comes with its own hardware wallet, the Hugware®. More about our plans in our White Paper.